 Heard enough about ransomware to last a lifetime? We get it. Hackers have accelerated their efforts for a quick payout that can cost you—in cash, your reputation, and even your business. As bad actors find workarounds in your security, one way that you can outsmart them is to take a more offensive approach with your storage.
Heard enough about ransomware to last a lifetime? We get it. Hackers have accelerated their efforts for a quick payout that can cost you—in cash, your reputation, and even your business. As bad actors find workarounds in your security, one way that you can outsmart them is to take a more offensive approach with your storage.
As a trusted solutions provider, iTBlueprint wants to help you elevate your security posture before a ransomware attack find its way to you. That’s why NetApp’s industry-leading enterprise data management software, ONTAP, is a gamechanger when it comes to everyday storage processes, as well as taking the pain out of ransomware.
Don’t Be Held Hostage
We’ve helped many of our customers recover from ransomware attacks, but the process isn’t always easy or pain free. Using NetApp Snapshot to make point-in-time, read-only copies of your data inoculates it from being infected by ransomware. Therefore, your data is exactly what it looked like at the moment the snapshot was taken, whenever that was—hours, days, weeks, months, or even years ago.
NetApp snapshots not only protect your backups from hostile encryption, they prevent deletion of valuable backup data. Plus restoring your data can be done quickly, we’re talking terabytes in seconds. But let’s first share some knowledge about how you can get the most out of snapshots for securing your data from a ransomware attack.
- Extinguishing the slow burn. Though you can restore from a snapshot that was taken before the attack, you need to have a retention policy to make sure you’re keeping copies long enough to recover your data. We recommend keeping snapshots for a few months since most ransomware have a nasty habit of lying dormant before it wreaks havoc on your data. With a few months of snapshots, you can recover quicker.
- Filling up instead of falling out. Since ransomware encrypts the file system, creating a higher rate of change, the extra storage and volume space will fill up quicker. Turn off autodelete so important data isn’t deleted just to make room for unrecoverable copies and ransomware-encrypted data.
Take Charge of Your Storage
One of the best features about ONTAP—and there are like 20 significant features that we could go on about—is that with NetApp Snapshot you can take charge of how you use your storage to get the most out of your space, as well as out of your investment.
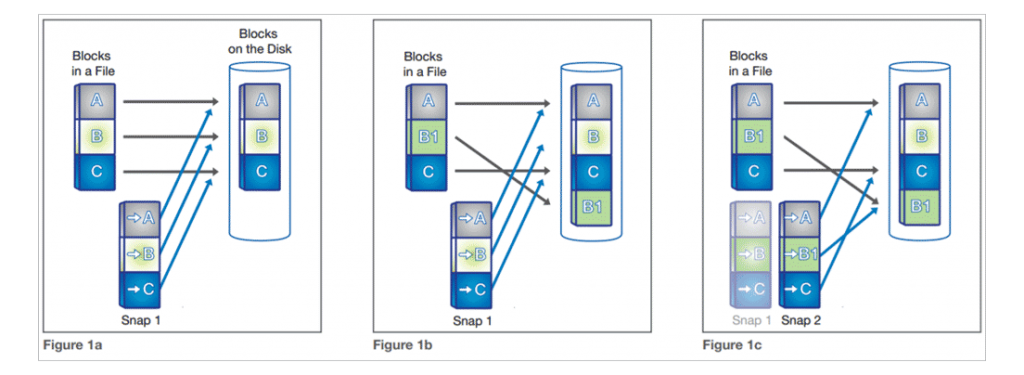
First of all, skip snapshot technology that uses Copy-On-Write (COW) which is slow and has a habit of causing performance issues. With COW, whenever there’s a change to the active file system data, the original data is moved into a special snapshot area on disk, and the changed data is written back to where the original data was located. This can take up a lot of space and make restoring your data very time consuming.
NetApp Snapshot copies use Redirect-On-Write (ROW), meaning instead of making a full copy, it only has to save whatever was changed at block level, taking up only incremental space each time. This means better storage efficiencies and quicker recovery.
This is especially important when working on projects that contain a lot of data. Think of how long it takes to save a Terabyte of data each time you backup. Since NetApp Snapshot only saves the changes that you made and not the entire file therefore exponentially increasing your speeds.
Lock It Down
 You can ramp up your storage protection by layering on NetApp SnapLock technology. While NetApp Snapshot can prevent data from being deleted automatically, mistakes happen that could leave you scrambling. Or worse, someone could steal your admin’s credentials and create chaos before you even know it.
You can ramp up your storage protection by layering on NetApp SnapLock technology. While NetApp Snapshot can prevent data from being deleted automatically, mistakes happen that could leave you scrambling. Or worse, someone could steal your admin’s credentials and create chaos before you even know it.
SnapLock is your write once, read many (WORM) compliance solution. NetApp SnapLock ensures that snapshot copies can’t be changed, renamed, or deleted until they’re aged out based on the configured policy. Once they’re committed to this non-erasable, non-rewriteable state, they’re locked in place, giving you an indefinite retention period.
Trust No One
 NetApp FPolicy helps you further elevate your ransomware protection strategy. The key is that FPolicy has a zero-trust engine, meaning it trusts no one. Zero trust provides you with extra security measures that go beyond permissions in access control lists.
NetApp FPolicy helps you further elevate your ransomware protection strategy. The key is that FPolicy has a zero-trust engine, meaning it trusts no one. Zero trust provides you with extra security measures that go beyond permissions in access control lists.
Initially intended to block unwanted files from being stored on your infrastructure, NetApp FPolicy can also block known ransomware too. FPolicy provides a file blocking methodology and file-access notification framework that allows organizations to monitor, filter or block traffic based on file extensions and file metadata.
Unfortunately, your people are one of your worst security gaps, especially when it comes to ransomware. One of your users just loves the video of a dog dancing and wants to save it for later. However, what if that mp4 has an encryption code built in underneath. They can still save whatever they want on their home folder, but if it’s a kind of file you’ve deemed unsavory, that file will never reach your network.
FPolicy also incorporates User Behavior Analytics (UBA) and pays attention to any inconsistencies in user patterns. If a user on your team seems to be acting weird—according to the analytics—their access can be denied, sending you a big red flag to take a look at what’s going on.

Infrastructure Architects
When you combine iTBlueprint’s years of experience and trusted know-how with ONTAP’s multitude of features, you can create a strong storage infrastructure environment that is versatile enough fit your business’s unique needs—spanning flash, disk and cloud.
As a NetApp Gold Partner, our team of experienced technicians understands the ins and outs of the NetApp product line. iTBlueprint empowers businesses to rethink the future, embrace cloud, and get the most out of their data with a foundation to store, manage, and protect it anywhere. From installation to upgrades to monthly management of your NetApp storage devices, iTBlueprint has the capabilities to provide you with end-to-end services for total support, when and where you need it.
Learn more about how iTBlueprint and NetApp can help you win the fight against ransomware.





